QStrike™ 6.0: Enterprise Quantum Security Assessment Platform
QStrike™ 6.0 is a comprehensive quantum security testing platform designed for enterprise environments. It proactively identifies cryptographic vulnerabilities before quantum threats emerge—ensuring your cryptographic infrastructure remains resilient against evolving quantum computing capabilities.
What's New in QStrike™ 6.0?
QStrike™ 6.0 introduces a comprehensive approach to cryptographic vulnerability assessment, helping organizations stay ahead of emerging threats.
Ephemeral Key Vulnerability Testing – Identifies cryptographic material leakage in logs, memory dumps, and debug outputs that can compromise encryption today.
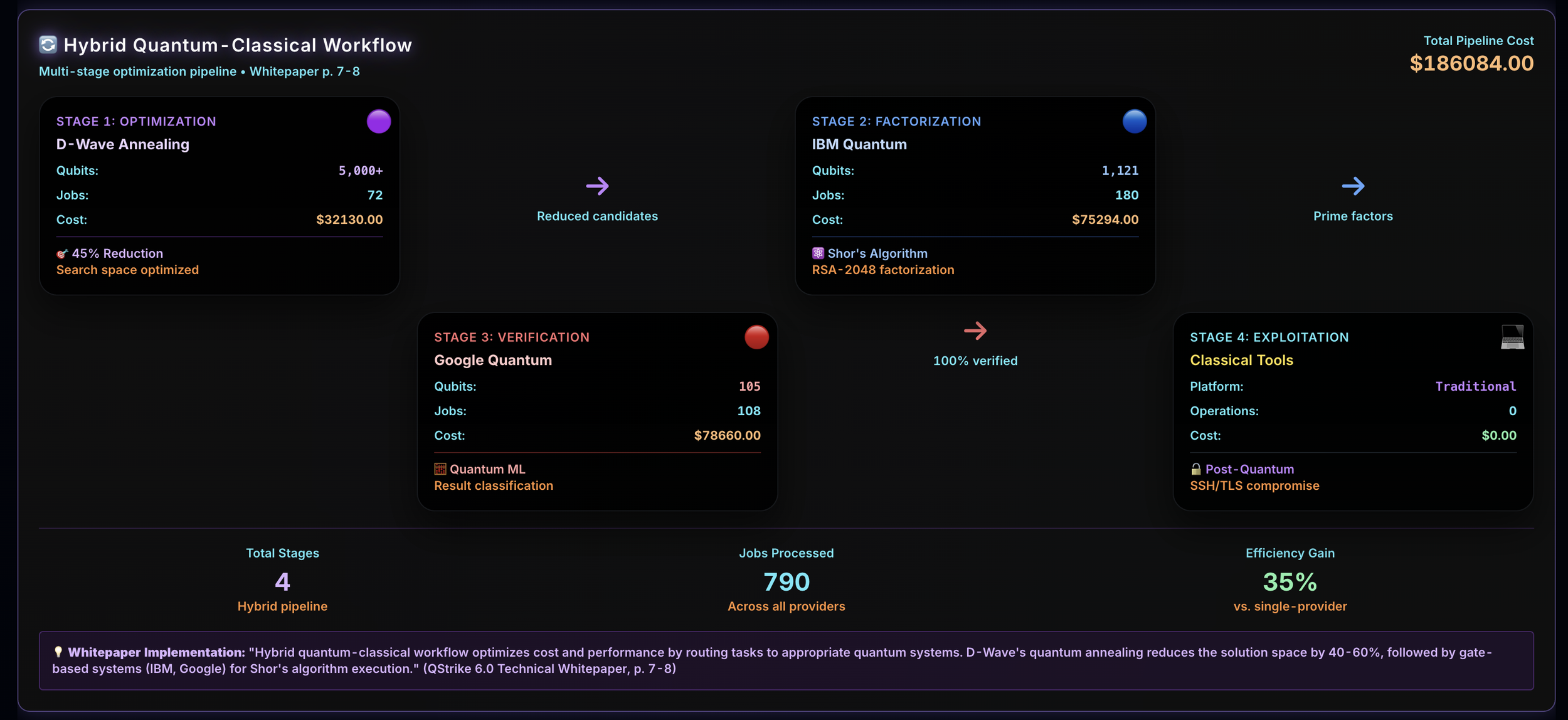
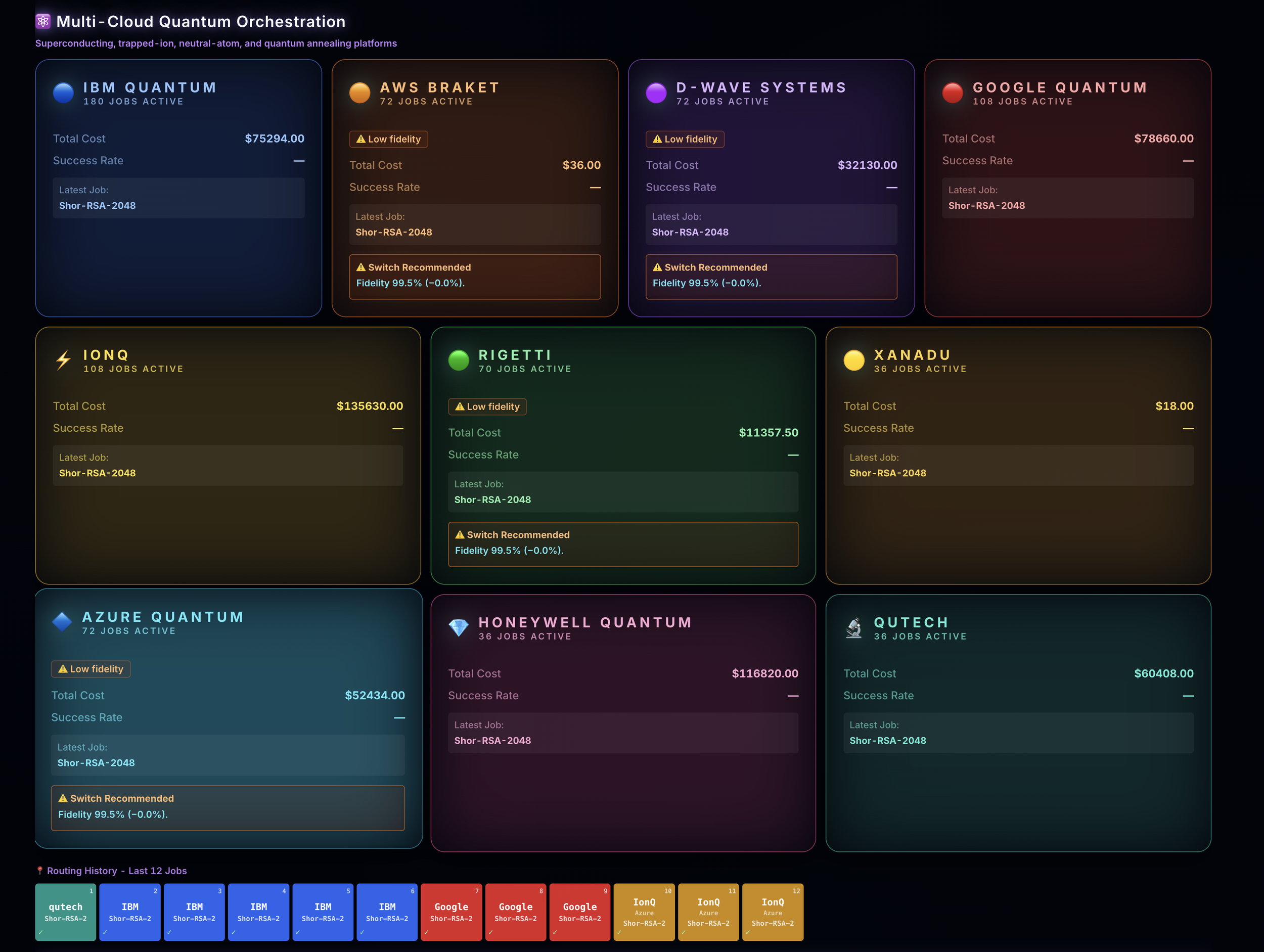
Multi-Cloud Quantum Testing – Leverages AWS Braket, IBM Quantum, Azure Quantum, IonQ, and D-Wave to validate cryptographic weaknesses.
LLM26 Integration – 70B parameter LLM specialized in cryptography and quantum computing orchestrates testing and analysis.
Compliance Readiness – Ensures enterprise alignment with NIST PQC standards and industry compliance frameworks.
Seamless Enterprise Integration – Works alongside existing cybersecurity frameworks for minimal-disruption risk mitigation.
“Quantum computing represents the biggest threat to data security in the medium term, since it can make attacks against cryptography much more efficient.”
— Marsh & McLennan Companies (Cybersecurity Risk Report)
How QStrike™ 6.0 Works
From discovery to permanent protection. We find what your current tools miss and fix it before attackers do.

Why Enterprises Choose QStrike™ 6.0
Proven Track Record – Over 300 vulnerabilities discovered across finance, healthcare, technology, and legal sectors during client engagements.
Dual-Threat Methodology – Addresses both immediate ephemeral key vulnerabilities (exploitable today) and future quantum computing threats.
Multi-Cloud Architecture – Works seamlessly within existing security stacks with no vendor lock-in.
Comprehensive Cryptographic Assessment – Future-proofs your encryption strategies to stay ahead of evolving quantum threats.
Current Cryptographic Vulnerabilities and Future Quantum Risks
Quantum computers are advancing faster than expected, and nation-state adversaries are already stockpiling encrypted data—anticipating future quantum computing capabilities that could compromise current encryption.
Organizations face two distinct threats: ephemeral key vulnerabilities exploitable today, and emerging quantum computing capabilities.
Ephemeral Key Vulnerabilities – Partial cryptographic material in logs, memory dumps, and debug outputs can reduce RSA-2048 factoring time from years to hours using current technology.
Harvest Now, Decrypt Later Attacks – Malicious actors collect encrypted data today to decrypt it when quantum power becomes available.
Post-Quantum Migration Timeline – Breaking RSA-2048 requires approximately 1 million physical qubits with error rates below 0.1%. Current systems have ~1,000 qubits, suggesting a 10-15 year timeline.
Qryptonic ensures your critical systems remain secure against both current and future cryptographic threats.
Organizations that delay quantum security testing risk catastrophic data exposure. QStrike™ 6.0 enables enterprises to simulate post-quantum threats today and implement preemptive security measures.”
— Cybersecurity Risk Advisory, Qryptonic

See What's Actually Exposed
45-minute technical briefing with our cryptographic security team. We'll show you real vulnerabilities we've found in environments like yours.
What You'll See
Live Ephemeral Key Detection
Watch QStrike™ find cryptographic material leaking in logs and memory that your current tools miss.
Real Quantum Hardware in Action
We'll run actual algorithms on IBM and AWS quantum computers against sample encrypted data.
Your Industry's Risk Profile
Anonymized findings from similar enterprises. See what vulnerabilities are most common in your sector.
NIST PQC Migration Roadmap
Clear timeline for Kyber, Dilithium, and SPHINCS+ adoption mapped to your compliance requirements.
They found key material in our debug logs that had been there for three years. Our pen testers never caught it.
Fortune 500 Financial Services
Most migrations take 18-24 months. Start now.